Search results
Spring Boot 3 and Spring Security 6 Digest Authentication Configuration
SecurityConfig.java:
@Configuration
@EnableWebSecurity
public class SecurityConfig {
@Value("${asimiotech.security.digest.key}")
private String digestKey;
@Value("${asimiotech.security.digest.nonce-validity-seconds:300}")
private int digestNonceValiditySeconds;
@Bean
public PasswordEncoder noOpPasswordEncoder() {
return NoOpPasswordEncoder.getInstance();
}
@Bean
@Primary
// Compatible with adding more password encoders in the future
public PasswordEncoder passwordEncoderDelegate() {
// Other password encoders
// ...
PasswordEncoder noOpPasswordEncoder = this.noOpPasswordEncoder();
Map<String, PasswordEncoder> encoders = new HashMap<>();
// ...
encoders.put("noop", noOpPasswordEncoder);
encoders.put(null, noOpPasswordEncoder);
// bcrypt for instance
return new DelegatingPasswordEncoder("<other than noop>", encoders);
}
@Bean
public UserDetailsService userDetailsService() {
UserDetails user1 = User.builder()
.username("username")
.password("password") // Has to be plain text, without {noop} prefix
.roles("USER_ROLE")
.build();
return new InMemoryUserDetailsManager(user1);
}
@Bean
public DigestAuthenticationEntryPoint digestAuthenticationEntryPoint() {
DigestAuthenticationEntryPoint result = new DigestAuthenticationEntryPoint();
result.setRealmName("Access to Web and API protected resources via Digest Auth");
result.setNonceValiditySeconds(this.digestNonceValiditySeconds);
result.setKey(this.digestKey);
return result;
}
@Bean
public DigestAuthenticationFilter digestAuthenticationFilter() {
DigestAuthenticationFilter result = new DigestAuthenticationFilter();
result.setUserDetailsService(this.userDetailsService());
result.setAuthenticationEntryPoint(this.digestAuthenticationEntryPoint());
result.setCreateAuthenticatedToken(true);
return result;
}
@Bean
public SecurityFilterChain basicSecurityFilterChain(HttpSecurity http) throws Exception {
http
.csrf(CsrfConfigurer::disable)
.authorizeHttpRequests(authorize -> {
authorize
.requestMatchers(
"/css/**",
"/error",
"/favicon.ico",
"/public/**",
"/webjars/**"
)
.permitAll()
.anyRequest()
.authenticated();
})
.exceptionHandling(ex ->
ex.authenticationEntryPoint(this.digestAuthenticationEntryPoint())
)
.addFilter(this.digestAuthenticationFilter());
return http.build();
}
}
application.yml:
asimiotech:
security:
digest:
key: 78309ce-657b3-cb043d0c-676888fa9-607
nonce-validity-seconds: 300
Usage
- Unhappy Path
curl -v http://localhost:8080/api/samples
> GET /api/samples HTTP/1.1
...
< HTTP/1.1 401
< WWW-Authenticate: Digest realm="Access to Web and API protected resources via Digest Auth", qop="auth", nonce="MTc0MzUyMjI5Mzk0MTowNzZlODY0ODBkNmVhMDkwZjhiZWI5NGQxZTgzZmI3Mw=="
...
- Happy Path
curl -v --digest --user username:password http://localhost:8080/api/samples
> GET /api/samples HTTP/1.1
...
< HTTP/1.1 401
< WWW-Authenticate: Digest realm="Access to Web and API protected resources via Digest Auth", qop="auth", nonce="MTc0MzYwNzMyMjkzOTpkYTc0MTY0Y2JhYjE4YjNkYmU4MmZlMjhmNDIyNWU0Nw=="
...
<
* Ignoring the response-body
* Issue another request to this URL: 'http://localhost:8080/api/samples'
* Server auth using Digest with user 'username'
...
> GET /api/samples HTTP/1.1
> Authorization: Digest username="username", realm="Access to Web and API protected resources via Digest Auth", nonce="MTc0MzYwNzMyMjkzOTpkYTc0MTY0Y2JhYjE4YjNkYmU4MmZlMjhmNDIyNWU0Nw==", uri="/api/samples", cnonce="MmI5OTM1M2M1NTRkNjdiNDg5MWIzMzgzMDBjNmZlM2U=", nc=00000001, qop=auth, response="9bb095bf3a1f3ac9f00734eb5ed0e984"
...
< HTTP/1.1 200
...
["Sample 1","Sample 2","Sample 3","Sample 4"]
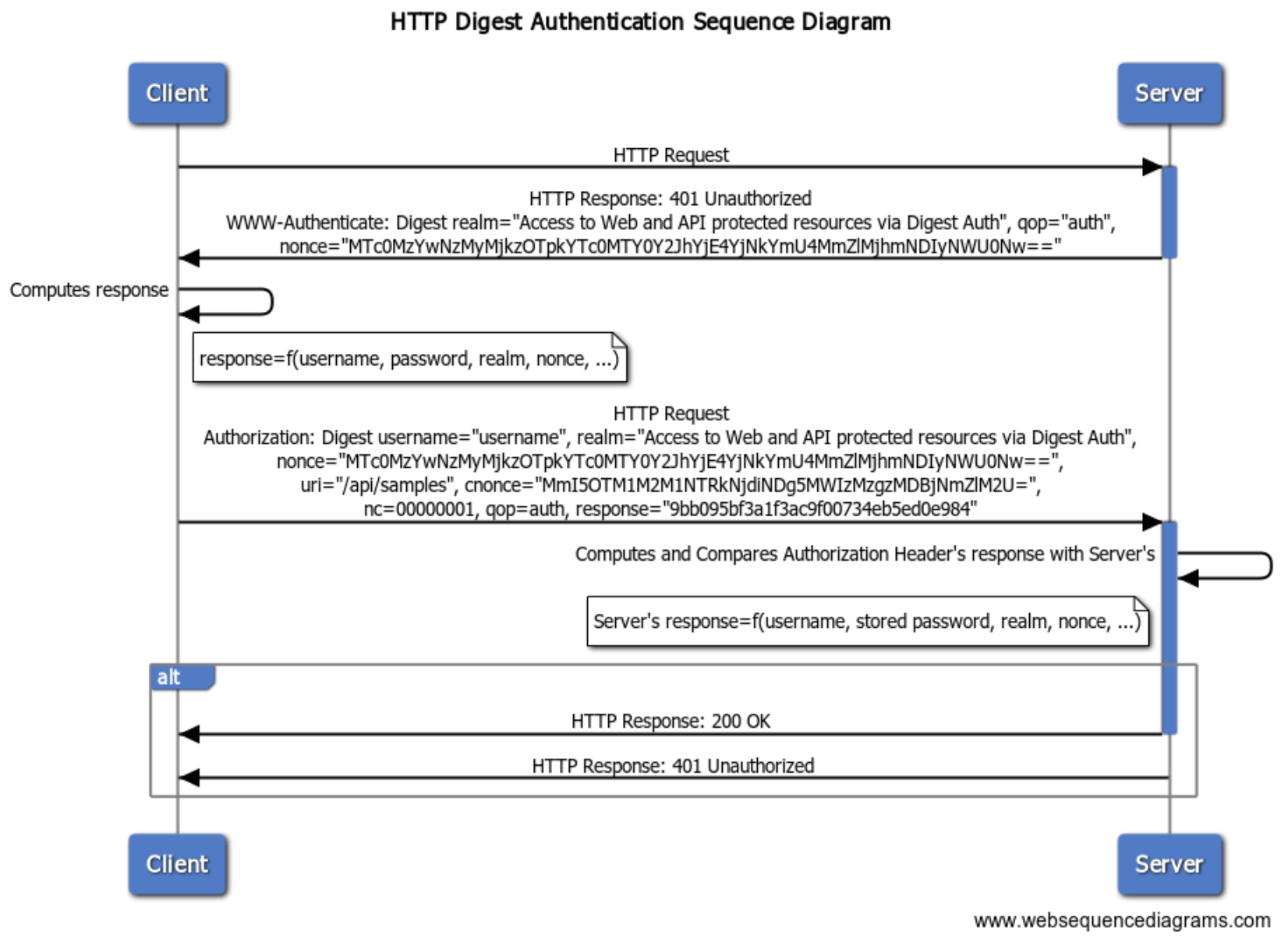 HTTP Digest Authentication Scheme Sequence Flow
HTTP Digest Authentication Scheme Sequence Flow




